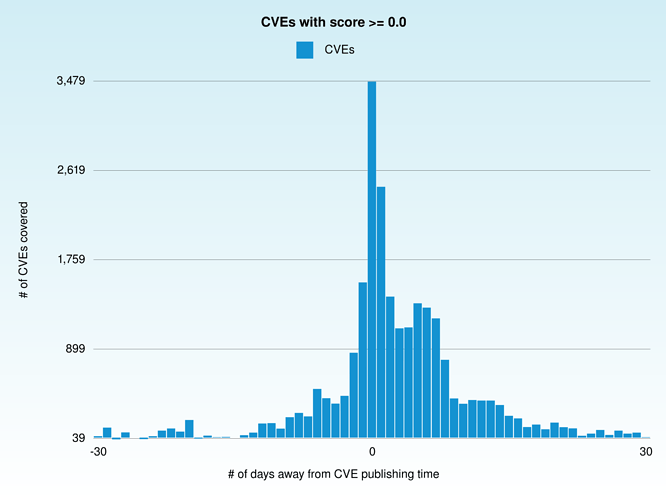
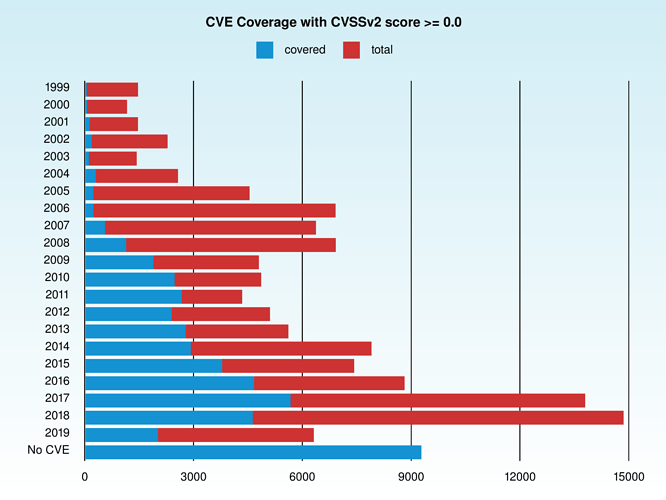
I am making a case for OpenVas 10, and one of the metrics I am interested is the average amount of days a given CVE takes to have a corresponding plugin on Openvas.
For the CVE publishing date, I used nvd feed (https://nvd.nist.gov/vuln/data-feeds#).
For Openvas10 plugin date, I used the get_nvts (https://docs.greenbone.net/API/OMP/omp.html#command_get_nvts) command to fetch the data about a given CVE plugin.
During my data processing, I found some interesting entries, like this:
CVE-2017-3106
openvas_creation: 2017-08-09T05:12:00Z publishing_time: 2017-08-11T19:29Z
Which basically told me that the plugin that deals with this CVE was made BEFORE (2-3 days) the publishing date for that CVE (https://nvd.nist.gov/vuln/detail/CVE-2017-3106):
<?xml version="1.0" encoding="UTF-8"?><get_nvts_response status=“200” status_text=“OK”>
Adobe Flash Player Security Updates( apsb17-23 )-Windows
<creation_time>2017-08-09T05:11:50Z</creation_time>
<modification_time>2019-07-17T11:14:11Z</modification_time>
3
General
<cvss_base>9.3</cvss_base>
97
registry
<cve_id>CVE-2017-3085, CVE-2017-3106</cve_id>
<bugtraq_id>NOBID</bugtraq_id>
<cert_refs>
<cert_ref type=“CERT-Bund” id=“CB-K17/1334” />
<cert_ref type=“DFN-CERT” id=“DFN-CERT-2017-1391” />
</cert_refs>
URL:https://helpx.adobe.com/security/products/flash-player/apsb17-23.html
cvss_base_vector=AV:N/AC:M/Au:N/C:C/I:C/A:C|summary=This host is installed with Adobe Flash Player
and is prone to multiple vulnerabilities.|vuldetect=Checks if a vulnerable version is present on the target host.|insight=The multiple flaws exists due to,
-
A security bypass vulnerability.
-
A type confusion.|impact=Successful exploitation of this
vulnerability will allow remote attackers to execute remote code and can get
sensitive information.|affected=Adobe Flash Player version before
26.0.0.151 on Windows.|solution=Upgrade to Adobe Flash Player version
26.0.0.151, or later.|solution_type=VendorFix|qod_type=registry
<preference_count>-1</preference_count>
<default_timeout />
</get_nvts_response>
At first I thought it was a mistake from my part, but I doubled checked everything and it is actually the case (for this example, like other occurrences):
Given my findings are accurate, as per the sources cited, this either means that the creation date of these plugins are inaccurate or that OpenVas somehow knows about vulnerabilities beforehand. Which one would be it? Thanks in advance.