Description
Linuxoid systems may have installed several kernels of which of course only one is active.
When doing an authenticated scan of such a system, we detect the kernels installed via the most common package managers like apt or RPM and if they are known to be vulnerable, then a vulnerability is reported. This is done for each found kernel and usually kernel vulnerabilities are of high severity.
It is recommended to simply delete the vulnerable kernels. The rationale is that this prevents the accidental start of the kernel which would expose a severe attack surface again.
However, since it is a quite common situation that many outdated kernels are still in the file system
and that this accumulates to a larger number of vulnerability findings when scanning a large server farm, we introduced an alternative to handle the most common Linux systems with less noise:
Solution / Configuration
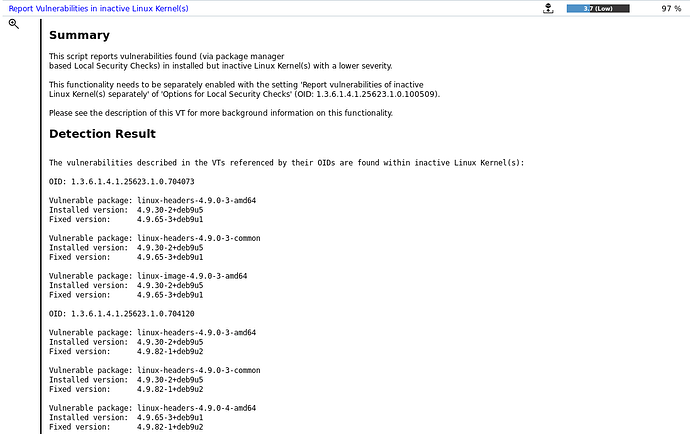
The VT Options for Local Security Checks offers the setting Report vulnerabilities of inactive Linux Kernel(s) separately where the default is no in all scan configurations.
If you create a new scan configuration or clone an existing one and change this setting to yes, then the VT Report Vulnerabilities in inactive Linux Kernel(s) will issue a result message with a severity of only 3.7 and list all found vulnerable (but inactive) kernels on the respective host while not reporting the vulnerabilities separately with a higher severity.
The severity of this Reporting-VT can be adjusted as usual with an override.