Reading a Report 
The results of a scan are summarized in a report. We can view reports directly on the web interface but also download them in different formats.
The appliance saves the reports of all the scans ever performed in a local database. This allows access to information from the past. All existing reports for all scans can be displayed by selecting Scans > Reports in the menu bar.
Once our scan has been started, we can view the report of the results found so far by clicking the bar in the column Status.
→ The details page of the latest report is opened. Results contains a list of all vulnerabilities detected by the appliance.
Note:
Your report will look different depending on your scanned target system.

Solution type 
Solution for the found vulnerability. The following solutions are possible:
A vendor patch is available.
A workaround is available.
A mitigation by configuration is available.
No fix is and will be available.
No solution exists.
Severity
The severity of the vulnerability is displayed as a bar to support the analysis of the results.
QoD
QoD is short for Quality of Detection and shows the reliability of the detection of a vulnerability.
By default, only results that were detected by VTs with a QoD of 70 % or higher are displayed. The possibility of false positives is thereby lower. The filter can be adjusted to show results with a lower QoD.
Host
Host for which the result was found. The IP address and the name of the host are displayed separately.
Location
Port number and protocol type used to find the vulnerability on the host.
Created
Date and time of the report creation.
Interpreting a Report
To interpret the results, note the following information:
False Positives
A false positive is a finding that describes a problem that does not actually exist. Vulnerability scanners often find evidence that point at a vulnerability, but a final judgment cannot be made. There are two options available:
Reporting of a potentially non-existent vulnerability (false positive).
Ignoring reporting of a potentially existing vulnerability (false negative).
Since we can identify, manage and as such deal with false positives compared to false negatives, the appliance reports all potentially existing vulnerabilities.
Multiple findings can have the same cause.
If an especially old software package is installed, often multiple vulnerabilities exist. Each of these vulnerabilities is tested by an individual VT and causes an alert. The installation of a current package will remove a lot of vulnerabilities at once.
High  and Medium
and Medium 
Findings of the severity levels High and Medium are most important and should be addressed with priority.
Before addressing medium level findings, high level findings should get addressed. This approach should only be deviated from in exceptional cases, e.g., if it is known that the high level findings need to be less considered because the service cannot be reached through the firewall.
Low  and Log
and Log 
Findings of the severity levels Low and Log are mostly interesting for detail understanding. These findings are filtered out by default but can hold very interesting information. Taking them into consideration will increase the security of the network and systems. Often a deeper knowledge of the application is required for a better understanding of a potential threat. Typically, a result with the severity Log involves a service that uses a banner with its name and version number. This could be useful for an attacker when this version has a known vulnerability.
Exporting a Report
The report of our task can be downloaded as follows:
1. Click in the upper left corner.
→ The scan report content composer is opened.
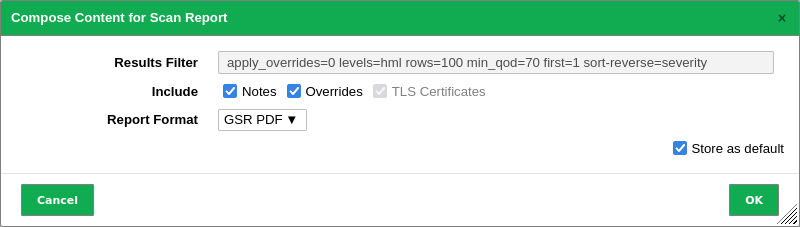
2. Select the report format in the drop-down list Report Format.
3. Activate the checkbox Store as default to save the settings for future exports.
4. Click OK.
5. Save the report by clicking Save File.
