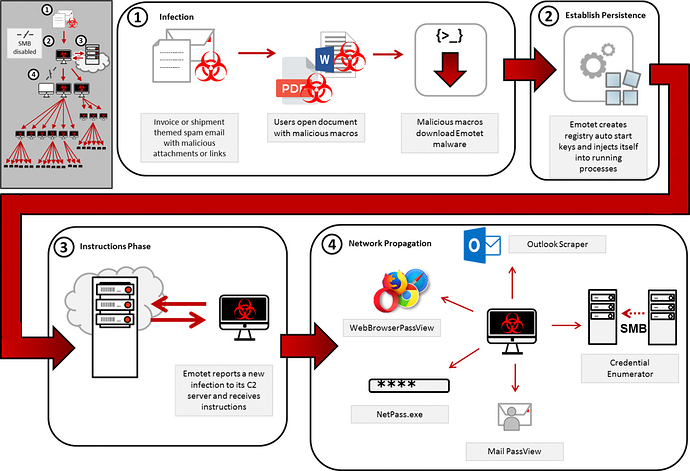
Description
Emotet is a Malware using multiple elements to create havoc in an infrastructure. Our Greenbone Security Feed now has a Vulnerability Test that checks for these elements. It strengthens your resilience and finds assets potentially compromised.
(Picture Source: Emotet Malware | CISA)
https://twitter.com/GreenboneEN/status/1074250594842525697
Additional to the detection of Emotet itself additional Policy/Compliance VTs (GSF only) have been created.
The attached scan configuration supports you to detect possible Misconfigurations and Vulnerabilities within your environment and to limit the initial attack vector via Microsoft Office Macros and the spreading of Emotet after the initial infection.
Emotet Detection
The VT Emotet Trojan Detection (OID: 1.3.6.1.4.1.25623.1.0.108521) checks and reports various Indicators of Compromise (IOCs) as a High level report entry.
Emotet Protection
The VT Disabled Macros for Office Applications (Emotet Protection) (OID: 1.3.6.1.4.1.25623.1.0.109713) gives a Log level report entry with a brief overview over the current Office Settings which are compliant and should help protecting you against Emotet. It also includes a list of items which needs to be reconfigured and the info what needs to be configured to be compliant.
Additional VTs are reporting recent SMB vulnerabilities and default credentials which might help Emotet to spread within your environment.
Scan Config
Note: The scan needs to be an authenticated scan against a Windows target (see Requirements on Target Systems with Windows for more information).
Compatiblitiy: Greenbone OS (GOS) or Greenbone Community Edition (GCE) < 6.0 / GVM < 11
emotet_scan_config.xml (646.5 KB)
Included VTs
| Name | Family | OID | Script preferences |
|---|---|---|---|
| Microsoft Outlook: Security setting for macros | Policy | 1.3.6.1.4.1.25623.1.0.109712 | |
| Microsoft Office Word: VBA Macro Notification Settings | Policy | 1.3.6.1.4.1.25623.1.0.109708 | |
| Microsoft Office PowerPoint: Block macros from running in Office files from the Internet | Policy | 1.3.6.1.4.1.25623.1.0.109711 | |
| Microsoft Office Word: Require that application add-ins are signed by Trusted Publisher | Policy | 1.3.6.1.4.1.25623.1.0.109703 | |
| Microsoft Office Word: Block macros from running in Office files from the Internet | Policy | 1.3.6.1.4.1.25623.1.0.109710 | |
| Microsoft Office Excel: Block macros from running in Office files from the Internet | Policy | 1.3.6.1.4.1.25623.1.0.109709 | |
| Microsoft Office PowerPoint: VBA Macro Notification Settings | Policy | 1.3.6.1.4.1.25623.1.0.109707 | |
| Microsoft Office PowerPoint: Require that application add-ins are signed by Trusted Publisher | Policy | 1.3.6.1.4.1.25623.1.0.109704 | |
| Microsoft Office Excel: VBA Macro Notification Settings | Policy | 1.3.6.1.4.1.25623.1.0.109706 | |
| Microsoft Office Excel: Require that application add-ins are signed by Trusted Publisher | Policy | 1.3.6.1.4.1.25623.1.0.109705 | |
| Microsoft Office: Check OLE objects | Policy | 1.3.6.1.4.1.25623.1.0.109702 | |
| Microsoft Windows: Status of Windows Script Host (WSH) | Policy | 1.3.6.1.4.1.25623.1.0.109701 | |
| Emotet Trojan Detection | Malware | 1.3.6.1.4.1.25623.1.0.108521 | “Run check” set to “yes” |
| Disabled Macros for Office Applications (Emotet Protection) | Compliance | 1.3.6.1.4.1.25623.1.0.109713 | |
| Compliance Tests | Compliance | 1.3.6.1.4.1.25623.1.0.95888 | “Launch Compliance Test” set to “yes” |